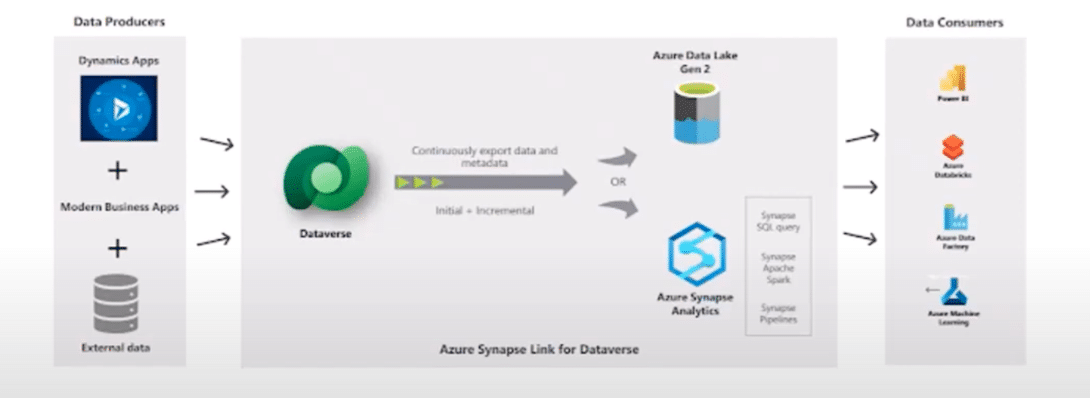
How to Set up Synapse Link for Dataverse to Enhance System Integration
With news that Microsoft is deprecating Export to Data Lake, a popular upgrade to replace this system has emerged in […]

With news that Microsoft is deprecating Export to Data Lake, a popular upgrade to replace this system has emerged in […]
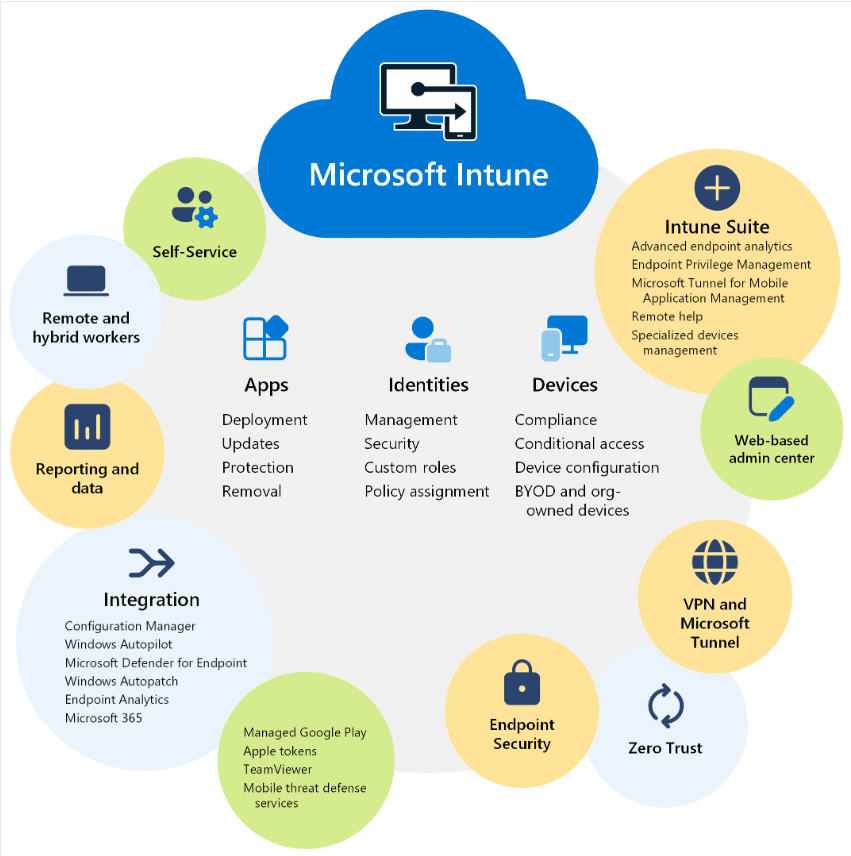
Microsoft Intune is instrumental in establishing a solid Microsoft Cloud security strategy, simplifying what can often be a time-consuming process. […]
While the thought of immediately using Microsoft’s new AI tool is exciting, there are several important things you need to […]
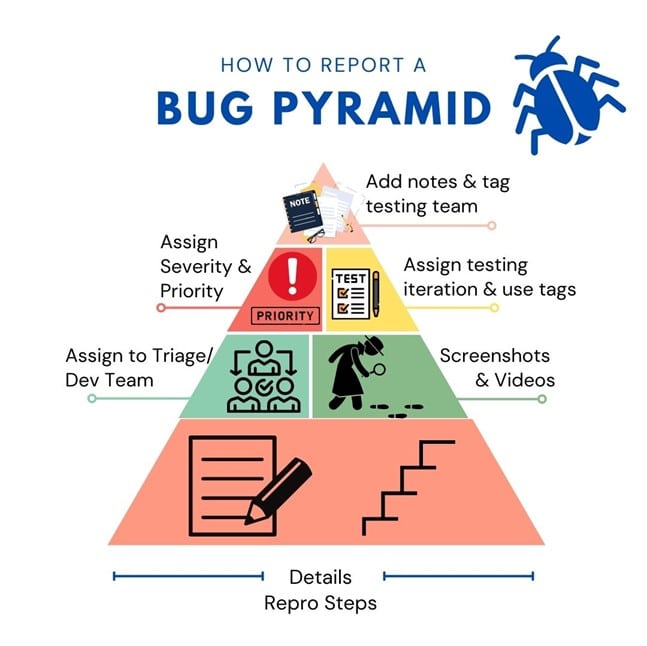
No matter what kind of business technology solutions you use, you are going to run into issues managing software bugs. […]
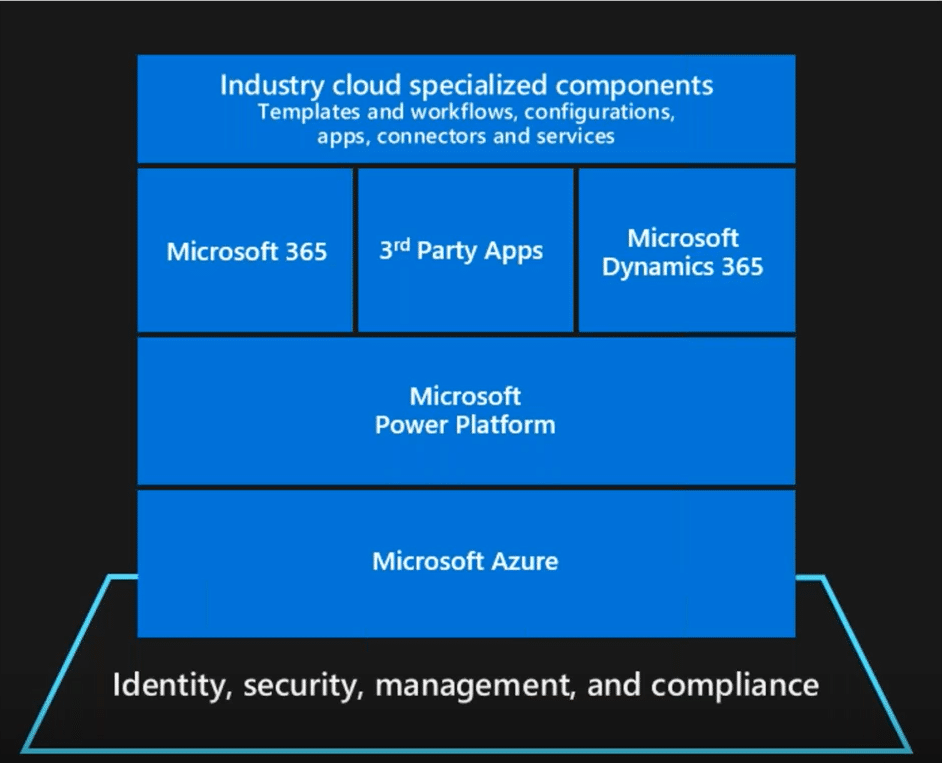
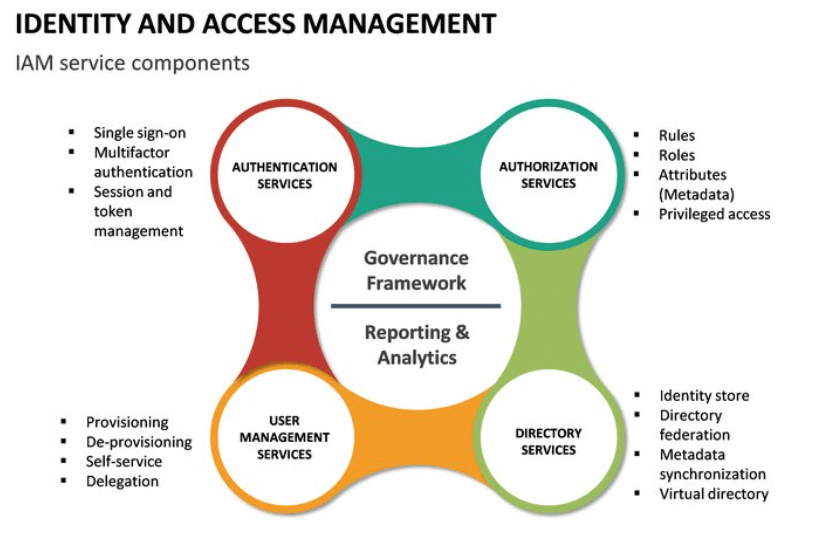
Identities within your organization are the keycards that give your users access to everything they need to do their jobs. […]
While the pandemic seems like a thing of the past to many, its effect on how and where we work […]

Cyber attacks are everywhere, and it’s becoming increasingly important to implement strong cyber security best practices to ensure your organizational […]
Testing Microsoft Dynamics software to ensure it works properly is an art and should be front of mind for all […]
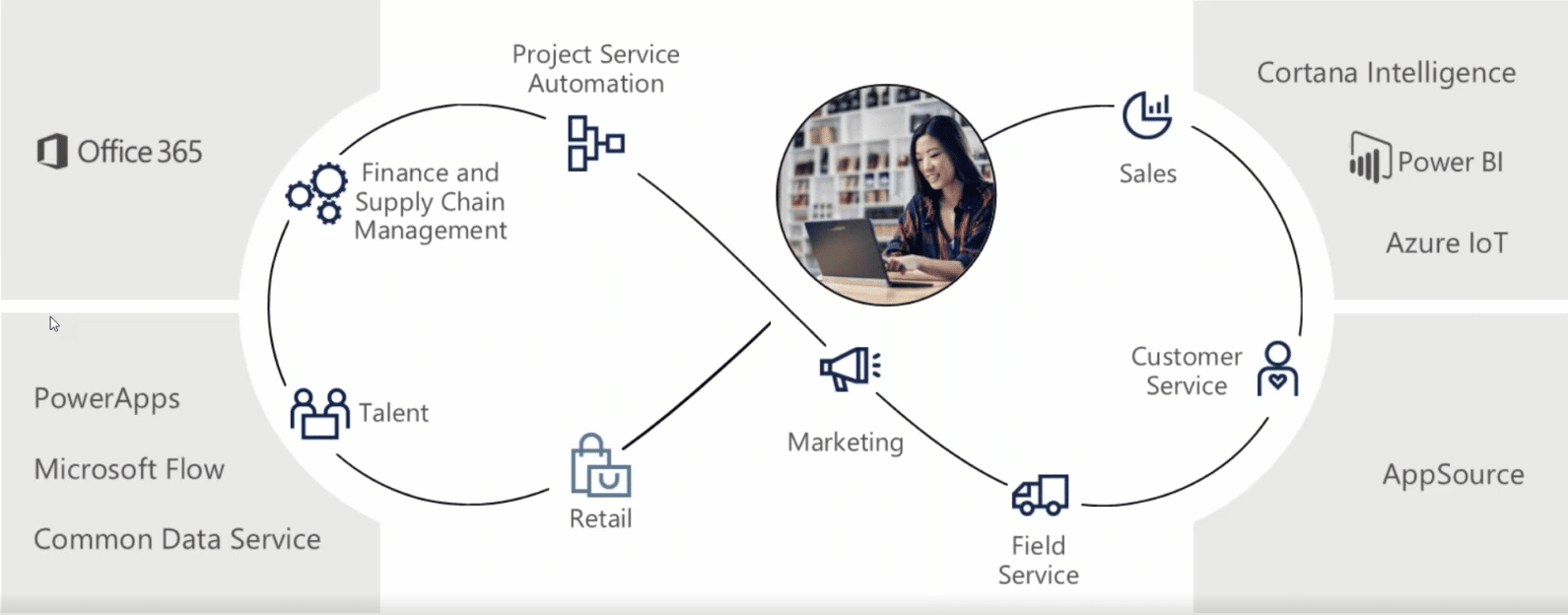
The time has never been better to upgrade from Dynamics AX to Dynamics 365 Finance and Operations. As more businesses […]

Top 7 Things You Can Do to Prepare Ransomware attacks have gone from an annoyance that the IT team talks […]
It’s our mission to help clients win. We’d love to talk to you about the right business solutions to help you achieve your goals.